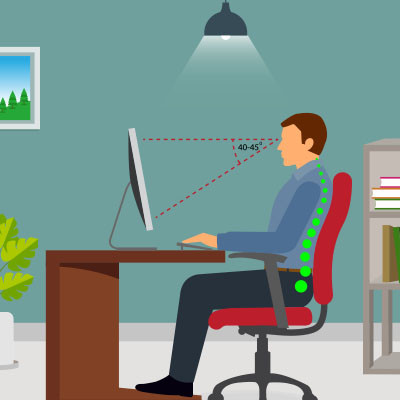
The strain on people’s bodies isn’t always taken seriously when someone works at a computer. Still, many official studies suggest that desk jobs can have a radical and rather negative effect on the health of individuals. One common ailment is what is called “tech neck.” Tech neck is a term that describes neck pain and damage stemming from looking down at computers or mobile devices for prolonged periods. To avoid tech neck, you can follow these helpful tips.

Patriot Tech Services Inc. Blog
Patriot Tech Services Inc. has been serving the Wheelersburg area since 2006, providing IT Support such as technical helpdesk support, computer support, and consulting to small and medium-sized businesses.
0 Comments
It’s an unfortunate fact that all businesses will inherently face some threats during their operations. That’s inescapable. From cyberattacks to natural disasters to good, old-fashioned accidents, you’re liable to face no small risk. This risk makes a process known as risk mitigation so critical for all businesses to undergo with some regularity.
Let’s review a few aspects of creating and maintaining a dependable risk mitigation strategy.
Business technology is known to be remarkably finicky, particularly if you do not have the requisite knowledge to manage and maintain it. After all, there is a reason why you hire an IT department or a managed service provider to handle this role. What happens if your technology fails, though? Do you have a plan in place? What does a plan like this even look like, anyway? Let’s dig into the details.
It’s always exciting when you can expand your business’ influence with a new location, but this excitement brings with it all kinds of complications. There’s always something, whether it’s the technology for the new location or the logistics surrounding the opening. Let’s look at how you can make sure that technology is not the thing that holds your business back from opening a new location.
Remote work offers numerous benefits for both your employees and your business, provided you can overcome the challenges associated with implementing it. One such challenge is productivity, something which employees might struggle with while working remotely. Here are four ways your average remote employee might be challenged by their remote work in terms of productivity.
Chances are, your and your employees’ lives are fully permeated with technology, from the very start of the day to the moment you close your eyes to sleep in the evening. That’s just how the world works nowadays, but there is evidence that this permeation of tech can have some adverse effects on us all. That’s why, as odd as it may sound coming from an IT provider, you may want to occasionally take a moment to step away from technology.
Your network is a crucial part of your business, insofar as it is quite literally what powers your operations and enables you to work productively… at least, most of the time. Unfortunately, there is always the risk of a network bottleneck, or a limited capacity for data to move due to a lack of available bandwidth. So, how can these bottlenecks be avoided?
With technology serving such an indispensable role in modern business the looming threat of disaster is one that needs to be considered. With so many consequences on the line, it’s important that your business is prepared to deal with these disasters effectively and efficiently. Let’s run through some tips for properly preparing for your potential disaster recovery needs.
Technology is important for many reasons, chief among them your business’ continued efficiency and productivity. The problem with technology, though, is that it will never last forever, and you’ll have to replace it sooner or later. Thankfully, you can delay those costs considerably by implementing a proactive technology management plan, effectively keeping the same technology running longer.
As the boss, you’re in a position to offload many of your business’ responsibilities to your employees. That’s more or less why you have employees in the first place. However, there’s more than one way that you can delegate tasks, depending on your personal style of management and the work style of each of your employees.
We’ve been examining the concept and phenomenon known as procrastination in recent weeks, touching on why we do it and how it often manifests itself in business processes. For our final few parts, we’ll be focusing on how you can stop procrastinating by utilizing both quicker, short-term tactics and long-term, sustained changes. Let’s start with some short-term tactics.
We recently started to pick apart the concept of procrastination as a means of understanding it better, and potentially, getting better at not doing it. Last time, we touched on a few ways that procrastination can potentially manifest, so it only made sense to us that we would continue pulling that thread and try to help you identify how you tend to procrastinate more specifically.
“Never put off until tomorrow what you can do today.” It’s timeless advice, as well as some of the easiest and most tempting advice to ignore. Procrastination is one of those things that we all assume we understand, but we wanted to take a bit of time to explore it in greater detail…and figure out how we can all work to resist it.
Your business depends on its bandwidth and its Internet connection to remain productive, part of which means ensuring that you have a reliable and stable wireless connection. How can you set up your network so that it is optimal and efficient? We have some thoughts on the matter and want to share them with you.
Back in 1995, the Association of Records Managers and Administrators were in the midst of campaigning for the renewal of the Paperwork Reduction Act. As a part of their efforts, they created National Records and Information Management Day. Over the years since, it has expanded into a week, and then into an entire month, for businesses around the world to consider their record-keeping practices.
Most people are capable of productivity, but sometimes it can come a bit harder for some than for others. If you find your staff have difficulty with consistency and productivity, we aren’t here to tell you methods for increasing their productivity; rather, we want to introduce a concept that is often overlooked when trying to get the most out of your team, and is a trait often found in the most productive people, and that is patience.
Tag Cloud
Best Practices
Information
Data
Security
Users
Business
Workplace Strategy
Quick Tips
Ransomware
Email
Technology
Collaboration
Business Management
IT Support
Network Security
Cybersecurity
Cloud
Small Business
Business Computing
IT Services
Hardware
Hackers
Google
Efficiency
Internet
Software
Innovation
Smartphones
Mobile Devices
Hosted Solutions
Productivity
Computer
Privacy
Communication
Workplace Tips
Phishing
Microsoft
Malware
User Tips
Tip of the Week
Sign Up For Our Newsletter
Latest Blog Entry
For the IT administrator and the small business owner, it can be a bewildering experience when your company comes under siege from employee-induced cyberthreats; especially if you, like many other companies, have started prioritizing security training. Even if the threat is ...
Latest News
Patriot Tech Services Inc. launches new website!
Patriot Tech Services Inc. is proud to announce the launch of our new website at www.patriot-techs.com. The goal of the new website is to make it easier for our existing clients to submit and manage support requests, and provide more information about our services for prospective clients.
Read more ...Account login
- Forgot Password
- No account yet? Register