For the IT administrator and the small business owner, it can be a bewildering experience when your company comes under siege from employee-induced cyberthreats; especially if you, like many other companies, have started prioritizing security training. Even if the threat is thwarted early and the effect on the business is negligible, it is important that you trust the people who have access to your organization’s digital resources. Let’s look at some of the reasons some of your staff take cybersecurity initiatives worse than others.

Patriot Tech Services Inc. Blog
Patriot Tech Services Inc. has been serving the Wheelersburg area since 2006, providing IT Support such as technical helpdesk support, computer support, and consulting to small and medium-sized businesses.
0 Comments
Businesses will often go into the process of self-improvement with unrealistic expectations for how much they can significantly improve their functionality. This simply is not true, and sometimes business owners need to realize that real change—the kind that yields real results—takes time. Thankfully, there are some actionable steps you can take to ensure that your business is moving in the right direction.
Technology can bring a lot of value for businesses, but sometimes it can be difficult to nail down exactly what can make a business run optimally. There are a lot of options, but all that means is that there are a lot of things that can potentially go wrong. Let’s take a look at some of the technology that small businesses are using to support the new workplace and create better opportunities.
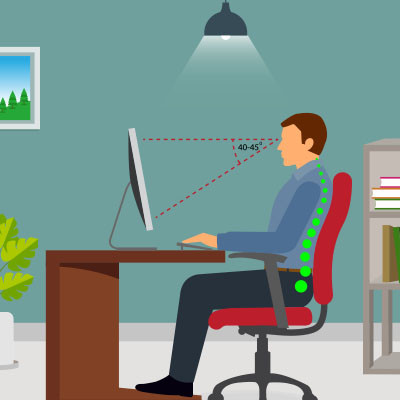
The strain on people’s bodies isn’t always taken seriously when someone works at a computer. Still, many official studies suggest that desk jobs can have a radical and rather negative effect on the health of individuals. One common ailment is what is called “tech neck.” Tech neck is a term that describes neck pain and damage stemming from looking down at computers or mobile devices for prolonged periods. To avoid tech neck, you can follow these helpful tips.
The laptop is an excellent piece of office equipment due to its portability and its power to meet the needs of most of today’s workforce. When in the office, however, many prefer the much larger screens that are more typical of the traditional desktop. Let’s talk about how you can get the best of both worlds by plugging your laptop into a set of peripherals and using it while it's closed—effectively turning it into a PC’s tower.
It’s an unfortunate fact that all businesses will inherently face some threats during their operations. That’s inescapable. From cyberattacks to natural disasters to good, old-fashioned accidents, you’re liable to face no small risk. This risk makes a process known as risk mitigation so critical for all businesses to undergo with some regularity.
Let’s review a few aspects of creating and maintaining a dependable risk mitigation strategy.
The constant fear of falling victim to scams has become a harsh reality and is far from ideal. However, the good news is that there is always time to acquire the skills needed to avoid such scams. Let's explore ways to enhance awareness regarding the challenges posed by scams, not only in a business context but also in everyday life.
Business technology is known to be remarkably finicky, particularly if you do not have the requisite knowledge to manage and maintain it. After all, there is a reason why you hire an IT department or a managed service provider to handle this role. What happens if your technology fails, though? Do you have a plan in place? What does a plan like this even look like, anyway? Let’s dig into the details.
It’s always exciting when you can expand your business’ influence with a new location, but this excitement brings with it all kinds of complications. There’s always something, whether it’s the technology for the new location or the logistics surrounding the opening. Let’s look at how you can make sure that technology is not the thing that holds your business back from opening a new location.
In the relatively short time it has been around, social media has fully ingrained itself into our lives, personally, professionally, and socially. While there are considerable benefits to be had in all of these areas, it is also undeniable that social media can easily become overwhelming and negatively impact us. For this reason, occasionally taking a break from social media isn’t a bad idea. Let’s go over a few ways to make this break as successful and effective as possible.
Templates are a handy feature that popular word processing platforms, like Google Docs, offer to help users create specific types of documents. While there are plenty of prebuilt templates available, there’s always the possibility that you have a need that isn’t filled by one of them.
In these cases, you always have the option to build your own. Let’s go over how, and discuss some of the elements and options that your custom Google Docs templates can support.
With the blockchain growing more popular as a technology, we thought it would be good to discuss how it works and why you should be aware of it. The zeitgeist often portrays it as a nefarious tool used by cryptocurrency and scams, but at its core, it is far from this; in fact, the applications of such a decentralized and transparent technology make it ideal for certain tasks. Let’s explore them.
If you are old enough to remember when antivirus (like most computer software) came in a great big textbook-sized box at the store, then you probably remember a time when that was the only protection you really needed.
Today, there are countless free versions of antivirus out there. Let’s talk about how much protection these actually bring, and when and where they might be a good fit.
Through cloud-based technology, your business can change the way it operates in countless different ways, all of which can benefit you in the long run. If you haven’t yet considered cloud-based solutions for infrastructure, then you could be missing out on some of the greatest innovations of the past decade. Here are some ways your business can start to leverage the cloud to its advantage.
This goes out to all the business owners, managers, department heads, and other leaders in the workplace who have to field user complaints and issues.
Being in this position can be hard, because you often have to say no. No, we can’t change the timeline or increase the budget for this project. No, we can’t do XYZ that way because it would break compliance. No, we can’t get new hardware/software in until we get it approved in the budget. Repeat ad nauseam.
We’re hoping that you are actually reading this post to prepare yourself if your business were to face a ransomware attack, but if you are suffering from one right now, we encourage you to reach out to us immediately, whether you are a client or not. Ransomware spreads quickly, and once it has infected a system, there really isn’t much you can do to stop it. However, there are steps you need to take to come back from this gracefully.
Do you remember a couple of years back when remote work went from being a privilege to the norm? It’s been a while since then, but many businesses have adopted hybrid or full remote operations, and as such, they are able to retain a semblance of normalcy even without the return of in-office work.
Some businesses have managed to get back to the state they were in prior to the pandemic, but there is a reason why a lot of businesses are not pushing the issue. Let’s go over some of them, and why forcing the issue with your employees is not necessarily a good idea.
Tag Cloud
Mobile Devices
Email
Security
Business Computing
Business
Hosted Solutions
Hackers
IT Support
Cybersecurity
Users
Smartphones
Efficiency
Small Business
Best Practices
Google
Network Security
Hardware
Cloud
Workplace Strategy
Innovation
Microsoft
Technology
IT Services
Workplace Tips
Malware
Ransomware
Computer
User Tips
Collaboration
Phishing
Productivity
Software
Information
Business Management
Quick Tips
Tip of the Week
Communication
Internet
Data
Privacy
Sign Up For Our Newsletter
Latest Blog Entry
For the IT administrator and the small business owner, it can be a bewildering experience when your company comes under siege from employee-induced cyberthreats; especially if you, like many other companies, have started prioritizing security training. Even if the threat is ...
Latest News
Patriot Tech Services Inc. launches new website!
Patriot Tech Services Inc. is proud to announce the launch of our new website at www.patriot-techs.com. The goal of the new website is to make it easier for our existing clients to submit and manage support requests, and provide more information about our services for prospective clients.
Read more ...Account login
- Forgot Password
- No account yet? Register